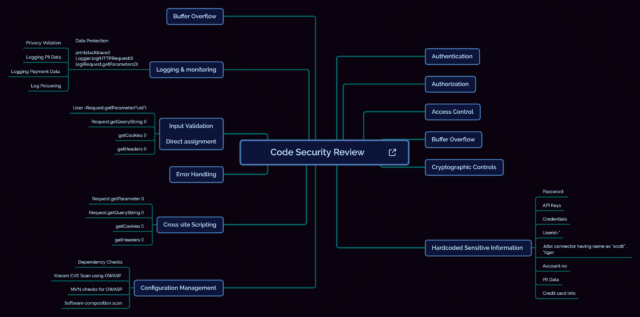
What is Security Code Review?
Process to review code and identify vulnerable/malicious code which can open up loopholes in the solution and may get exploited to have impact on Confidentiality, Integrity & availability of system in place. It is a process under which an application or programming source code are inspected or examined by an individual or team, known as Security Code Reviewers.
These Security Code Reviewers perform the analysis of the source code: either physically or by utilizing industry recognized automated tools for code review. Code Review best practices focuses on various areas including OWASP top 10. Few of the critical areas to look for when you create your next code review checklist:
Process
Now the question arises as to how to do code review? Primarily security reviewers perform this activity either by doing automated analysis termed as “Automated Code security Scanning” followed by manual analysis and removal of false positives which is termed as “Manual Security Code Review”
Manual approach rely more on the skillset/capability of consultant/ reviewer to read through code and understand the vulnerable areas in code. It is a bit more strategic approach as Compared to Automated approach.
1. Input Validation:
Input Validation is performed to ascertain the input being accepted by application is getting validated appropriately and qualified information is entering the work processes of the application frameworks. Attackers use unvalidated input calls entry points to inject payloads and exploit systems in place.
The following checks can be performed on methods to identify unvalidated input from the attacker.
- from URL parameters in
javax.servlet.HttpServletRequestclassgetParameter ()method - Form fields in javax.servlet.HttpServletRequest class getQueryString () method
- Cookies javax.servlet.HttpServletRequest,/code> class getCookies () method
- from HTTP headers javax.servlet.HttpServletRequest,/code> class getHeaders () method
The following sample can be taken as the example of unvalidated input vulnerability.
Bad Code:
Iterator iter = request.getParameterNames();
While(iter.hasNext())
{
String paramName = (String) iter.next();
System.out.println (paramName +request.getParameter (paramName));
}
Remediation:
To eradicate the loopholes which were generated through the unvalidated input either we have to create a list of valid characters termed as “Whitelist” or cleaning and rejecting the malicious input e.g. { ( @$%&- } etc. termed as “Blacklist”.
Following Codes can be used as a reference to implement validation and improve the vulnerable code.
Iterator iter = request.getParameterNames();
String input = request.getParameter ("input");
String characterPattern = "/ [^A-z]/";
If (! input. matches (characterPattern))
{
out.println (“Invalid Input”);
}
2. Command injection:
The attacker aims to attack the host operating system in order to gain access by injecting some arbitrary commands using a vulnerable application.
The following sample code is the example of Command injection vulnerability.
Class Execclass {
public static void main (String args []) {
Runtime rt = Runtime.getRuntime ();
Process proc = rt.exec (“cmd.exe /C”);
}
}
3. Cross Site Scripting:
The attacker injects some malicious code within a web application or web page and the web application or web page becomes a channel to deliver malicious code scripts to the user browsers. This enables an attacker to take over the DOM object including unprotected cookies allowing Account take over scenarios.
The following sample code is the example of XSS vulnerability.
Iterator iter = request.getParameterNames ();
While (iter.hasNext ())
{
String paramName = (String) iter.next ();
out.println (paramName +request.getParameter (paramName));
}
4. Improper Cookie Management
Improper Cookie management gives rise to cookie poisoning and privilege escalation vulnerabilities within the application.
The following vulnerable code set the cookie as persistent and stored in the local system for one hour.
Public class SetCookie extends HttpServlet
{
Public void doGet ()
{
Cookie cookie = new Cookie ("Session Cookie” + value);
cookie.setMaxAge (3600);
response.addCookie (cookie);
}
It is also important to do SCA (Composition Analysis & IP scans ) to find out any infringements or licensing violations and it can be performed using:
- Owasp dependency checker:
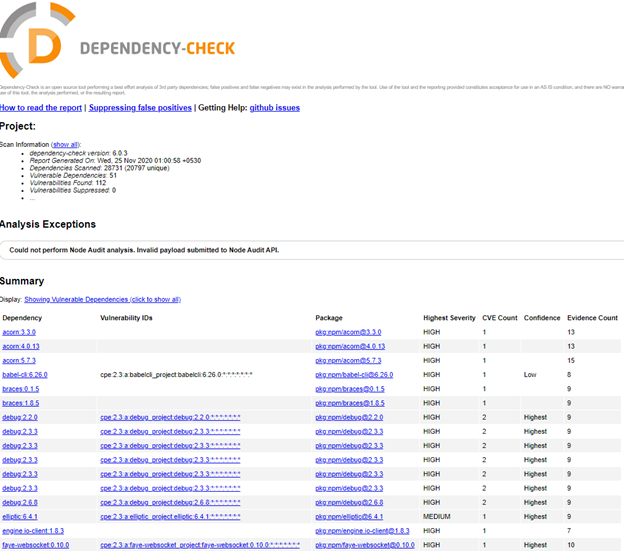
Dependency-Check is a Software Composition Analysis (SCA) tool that searches a project’s dependencies for publicly documented vulnerabilities. It accomplishes this by assessing whether a dependent has a Common Platform Enumeration (CPE) identifier. If it is found, it will generate a report with links to the CVE entries.
There is a command line interface, a Maven plugin, an Ant job, and a Jenkins plugin for dependency-check. The core engine has a set of analyzers that look at the project dependencies and collect data about them (referred to as evidence within the tool). The evidence is then utilised to determine the dependency’s Common Platform Enumeration (CPE).
If a CPE is found, a report is generated with a list of related Common Vulnerability and Exposure (CVE) entries. For certain technologies, third-party services and data sources such as the NPM Audit API, the OSS Index, RetireJS, and Bundler Audit are used.
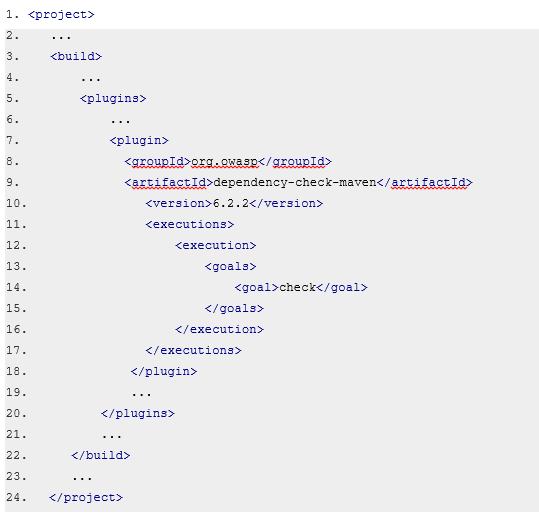
2. Maven Dependency Check:
It is a type of plugin that is used to identify publicly documented vulnerabilities in the project’s dependencies. The plugin will generate a report that includes the dependency, any discovered Common Platform Enumeration (CPE) identifiers, and the CVE entries associated with them. Create the dependency-check-report.html in the target directory.
Conclusion:
One of the various approaches for ensuring software security is to conduct security code reviews. They enable the reviewer to check numerous control objectives that are impossible to test using other approaches, and hence can be used to provide reasonable assurance that the software meets a certain set of (security) control objectives.


