Lets Scrutinize AWS Cloud
Amazon Web Services (AWS) is the world’s most comprehensive and widely adopted cloud computing platform, with over 200 fully featured services available from data centres around the world. AWS offers more services and features than any other cloud provider, ranging from traditional infrastructure technologies like computation, storage, and databases to emerging technologies like machine learning and artificial intelligence, data lakes and analytics, and the Internet of Things. AWS is designed to be the most adaptable and secure cloud computing platform available.
AWS and the customer share responsibilities for security and compliance. As AWS operates, administers, and controls the components from the host operating system and virtualization layer down to the physical security of the buildings in which the service works, this shared model can assist ease the customer’s operational burden. The customer is responsible for the guest operating system, other associated application software, and the setting of the security group firewall provided by AWS.
AWS duty “Cloud Security” – AWS is in charge of safeguarding the infrastructure that underpins all of the AWS Cloud’s services. The hardware, software, networking, and facilities that run AWS Cloud services make up this infrastructure.
Customer responsibility “Security in the Cloud” – The AWS Cloud services that a customer chooses will define their obligation. This specifies how much setup effort the customer is responsible for as part of their security obligations.
Borderline Checks for Pentesting AWS Cloud
According to the aws shared security model, the customer is responsible for security of services which are operationalized by the customer itself. Additionally aws offers to carry out security assessments or penetration tests against their aws infrastructure without prior approval for 8 services, which are:
-
- Amazon EC2 instances, NAT Gateways, and Elastic Load Balancers.
- Amazon RDS.
- Amazon CloudFront.
- Amazon Aurora.
- Amazon API Gateways.
- AWS Lambda and Lambda Edge functions.
- Amazon Lightsail resources.
- Amazon Elastic Beanstalk environments.
A crucial note taking point here is that customers aren’t permitted to conduct any security assessments of aws infrastructure or services themselves. AWS has aligned a policy set for customers to perform penetration testing. This policy also comprises some prohibited activities, which are:
-
- DNS zone walking via Amazon Route 53 Hosted Zones.
- Denial of Service (DoS), Distributed Denial of Service (DDoS), Simulated DoS.
- Port flooding.
- Protocol flooding.
- Request flooding (login request flooding, API request flooding).
Gearing-Up Arsenal for Cloud Security
As a pentester, we always seek tools and techniques which can exponentially speed up the process and boost the overall performance. It’s time for such gizmos which can take the game to a whole new level.
-
- Scoutsuite

Scout Suite is an open source multi-cloud security-auditing application that allows cloud infrastructures’ security posture to be assessed. Scout Suite gathers configuration data for manual examination and indicates risk areas using APIs given by cloud providers. Scout Suite automatically gives a clear image of the attack surface rather than navigating through dozens of pages on web interfaces. Once this has completed, it will generate an HTML report including findings and cloud account configuration
- Scoutsuite
-
-
- Cloudsploit
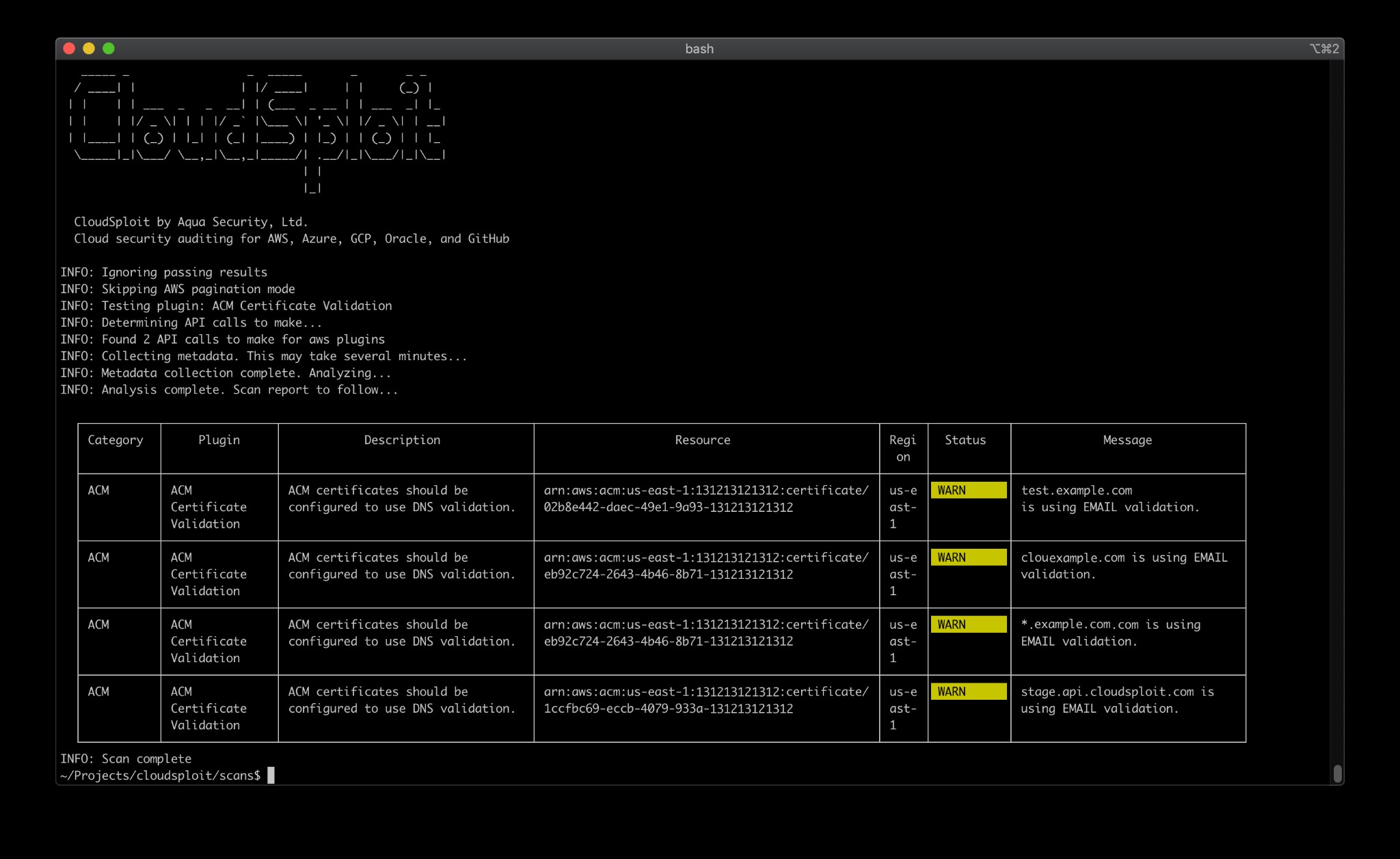
Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), Oracle Cloud Infrastructure (OCI), and GitHub are among the cloud infrastructure accounts that CloudSploit by Aqua can discover security issues in. These scripts are intended to return a list of probable security vulnerabilities and misconfigurations.
- PMapper
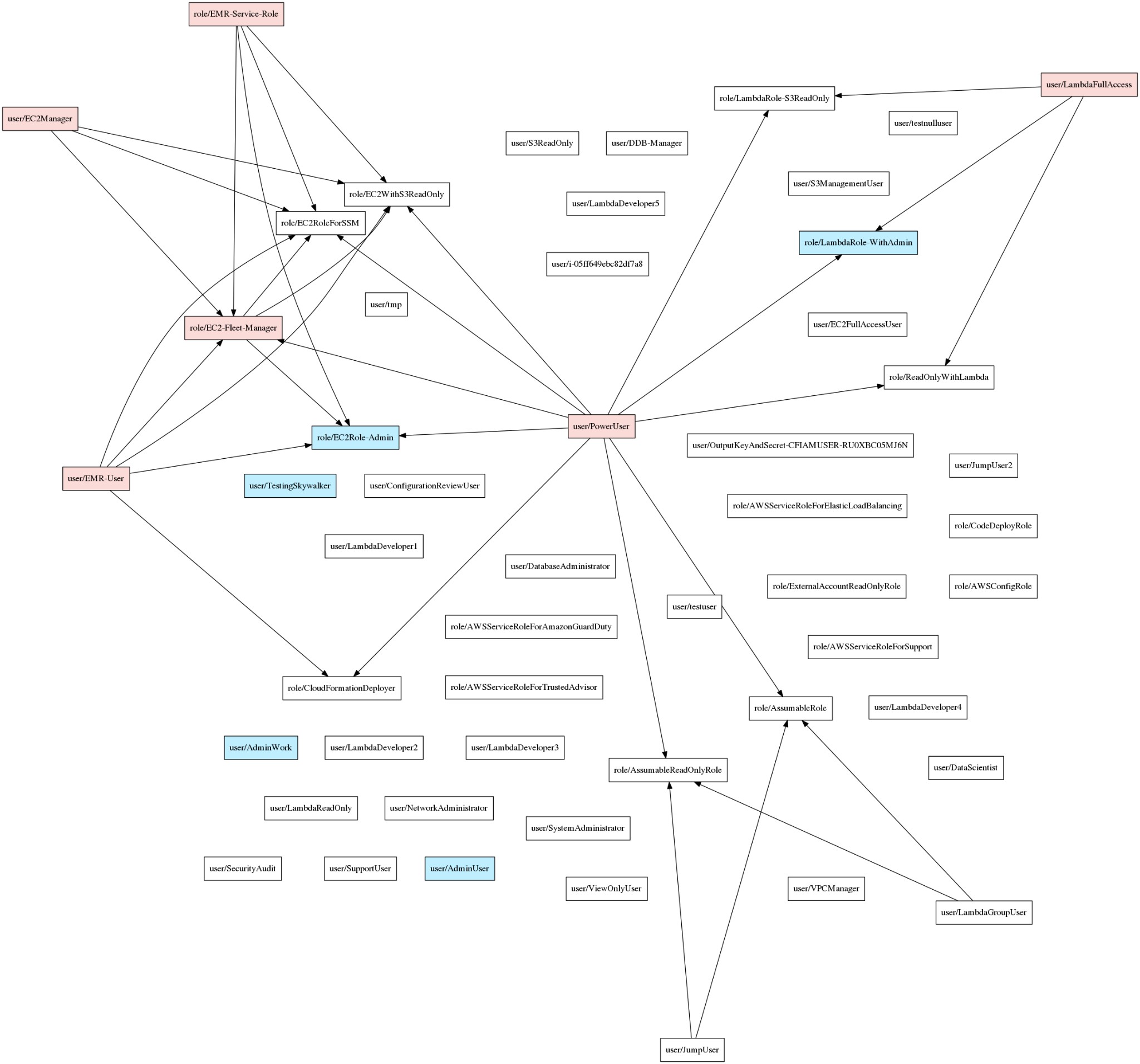
PMapper (Principal Mapper) is a script and library for detecting hazards in AWS Identity and Access Management (IAM) configuration for an AWS account or an AWS organisation. It uses a directed graph to simulate the different IAM Users and Roles in an account, allowing checks for privilege escalation and alternative paths an attacker could take to get access to an AWS resource or action.
- AWS Consoler
$> git clone https://github.com/NetSPI/aws_consoler<br />$> aws_consoler -v -a AKIA[REDACTED] -s [REDACTED]<br 2020-03-13 19:44:57,800 [aws_consoler.cli] INFO: Validating arguments... 2020-03-13 19:44:57,801 [aws_consoler.cli] INFO: Calling logic. 2020-03-13 19:44:57,820 [aws_consoler.logic] INFO: Boto3 session established. 2020-03-13 19:44:58,193 [aws_consoler.logic] WARNING: Creds still permanent, creating federated session. 2020-03-13 19:44:58,698 [aws_consoler.logic] INFO: New federated session established. 2020-03-13 19:44:59,153 [aws_consoler.logic] INFO: Session valid, attempting to federate as arn:aws:sts::123456789012:federated-user/aws_consoler. 2020-03-13 19:44:59,668 [aws_consoler.logic] INFO: URL generated! https://signin.aws.amazon.com/federation?Action=login&Issuer=consoler.local&Destination=https%3A%2F%2Fconsole.aws.amazon.com%2Fconsole%2Fhome%3Fregion%3Dus-east-1&SigninToken=[REDACTED
A utility to convert your AWS CLI credentials into AWS console access.
- Cloudsplaining
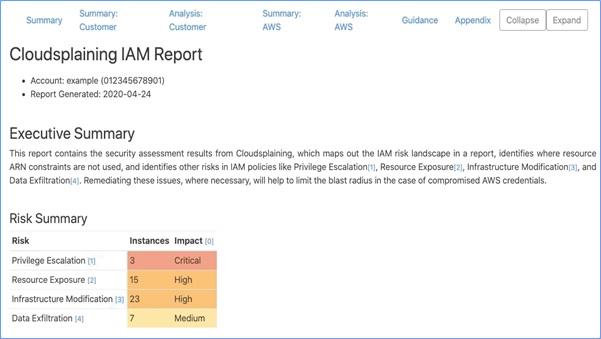
Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report.
- Pacu
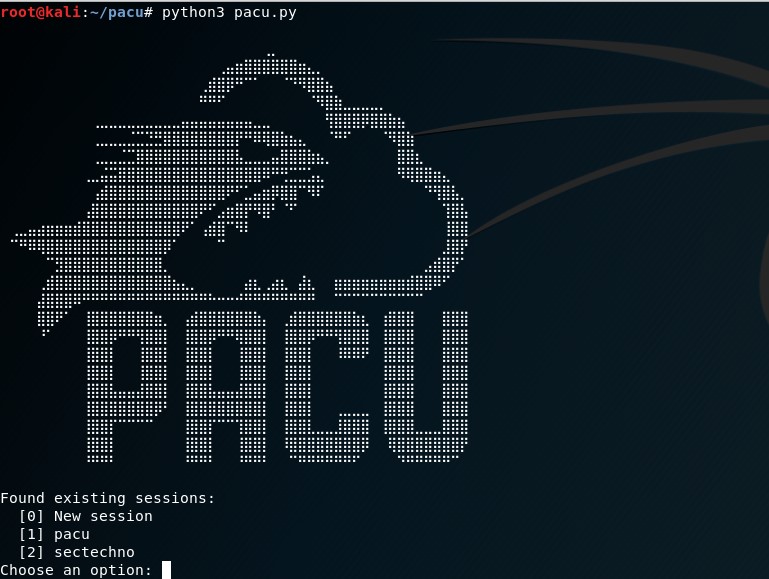
Pacu is an open-source Amazon Web Services (AWS) exploitation framework for offensive security testing in cloud settings. Pacu is a tool developed and maintained by Rhino Security Labs that allows penetration testers to exploit configuration weaknesses within an AWS account while also allowing them to quickly expand its functionality with modules. User privilege escalation, backdooring of IAM users, attacking weak Lambda functions, and other attacks are all possible with the current modules.
- Enumerate-iam
git clone [email protected]:andresriancho/enumerate-iam.git pip install -r requirements.txt ./enumerate-iam.py --access-key AKIA... --secret-key StF0q... 2019-05-10 15:57:58,447 - 21345 - [INFO] Starting permission enumeration for access-key-id "AKIA..." 2019-05-10 15:58:01,532 - 21345 - [INFO] Run for the hills, get_account_authorization_details worked! 2019-05-10 15:58:01,537 - 21345 - [INFO] -- {<br /> "RoleDetailList": { "Tags": [], "AssumeRolePolicyDocument": { "Version": "2008-10-17", "Statement": [ { ... 2019-05-10 15:58:26,709 - 21345 - [INFO] -- gamelift.list_builds() worked! 2019-05-10 15:58:26,850 - 21345 - [INFO] -- cloudformation.list_stack_sets() worked! 2019-05-10 15:58:26,982 - 21345 - [INFO] -- directconnect.describe_locations() worked! 2019-05-10 15:58:27,021 - 21345 - [INFO] -- gamelift.describe_matchmaking_rule_sets() worked! 2019-05-10 15:58:27,311 - 21345 - [INFO] -- sqs.list_queues() worked!
List the rights that come with your AWS credentials. This tries to make all API calls allowed by the IAM policy using brute force. All of the calls made by this tool are non-destructive.
- AWS Inventory
This is a tool that tries to find all of the AWS resources that have been created in a given account. The ecosystem allows customers to combine a variety of services to create a unique cloud experience. The ability to quickly spin up services at scale comes at a cost in terms of manageability. Auditing an AWS account for the resources used can soon become complicated.
- Prowler
Prowler is a command-line tool for assessing, auditing, hardening, and responding to AWS security incidents. It follows the CIS Amazon Web Services Foundations Benchmark requirements (49 checks) and has over 100 extra checks, including GDPR, HIPAA, PCI-DSS, ISO-27001, FFIEC, SOC2, and other regulations.
- Skyark
-
$ git clone https://github.com/cyberark/SkyArk $ powershell -ExecutionPolicy Bypass -NoProfile PS C> Import-Module .\SkyArk.ps1 -force<br />PS C> Start-AWStealth or in the Cloud Console PS C> IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/cyberark/SkyArk/master/AWStealth/AWStealth.ps1') PS C> Scan-AWShadowAdmins
Discover the most privileged users in the scanned Amazon Web Services environment, including shadow admins.
-
-
Conclusion
The takeaway from this blog article is that many businesses are fast migrating to cloud-based infrastructure. It is likely that in the not-too-distant future, the customer will not own any physical infrastructure. Everything will instead be converted into cloud services. It’s past time for pentesters to recognise that the cloud has become their new playground. One can boost their game by improving their understanding of the cloud ecosystem and the precise strategy to pentesting the cloud environment.
ABIR Networks can help you by providing best in class solutions for Cloud Penetration Testing requirements. Click here to set up a call/talk to sales team.


